A new global botnet that has been used for large-scale denial of service attacks is built on lightly secured home broadband routers in Brazil, Thailand and other developing nations, according to a report from the firm Incapsula.
In a report shared with The Security Ledger and released on Tuesday, Incapsula researchers said that the botnet consists of a large number of SOHO (small office and home office) routers, many of them Ubiquiti home routers equipped with ARM processors. Incapsula recorded traffic from more than 40,000 IP addresses associated with 1,600 ISPs worldwide. 85% of the compromised routers were located in Thailand and Brazil, the company said.
As is often the case with attacks on home routers, the Incapsula researchers found that the devices were easy prey for enterprising cyber criminals. An investigation revealed that the compromised units were remotely accessible via HTTP and SSH on their default ports and all were configured with vendor-provided default login credentials.
Insecure home broadband routers are an endemic problem made worse as the devices have become an attractive target for cyber criminals, especially as security improvements and feature upgrades have made home PCs more challenging to compromise. In October, the firm Rapid7 warned about a vulnerability in more than 1 million SOHO routers makes them potentially vulnerable to remote attacks that could expose private internal network traffic to prying eyes. In that case, the culprit was implementation and configuration vulnerabilities in NAT-PMP features. In September researchers at the firm Sucuri warned of a web-based attack launched from the site of a popular Brazilian newspaper that was targeting home broadband routers. And, in July, the Electronic Frontier Foundation launched the Open Wireless Router Project to develop a secure alternative to commercial SOHO routers that are more secure and can operate in a peer-to-peer mode.
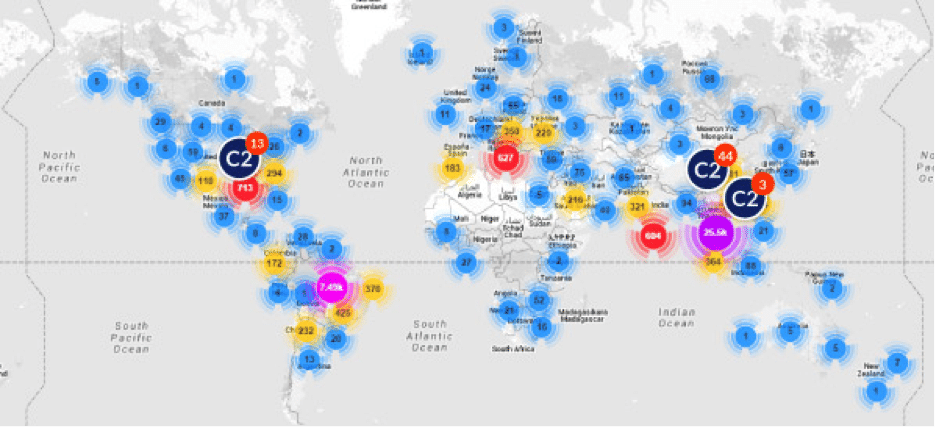
Incapsula recorded malicious traffic from 109 countries. Brazil and Thailand were the source of 85 percent of all traffic.
Ubiquiti (NADAQ: UBNT) is the brainchild of Robert Pera, a former Apple Engineer who launched the company in 2005. Around 70% of Ubiquiti’’s revenue comes from developing countries including Brazil, Indonesia and the Czech Republic, where the company sells through a global network of distributors.
“Ubiquiti Networks tried to do a good thing and bring internet connection to third world regions this year, unfortunately it’s just been discovered that their routers are being actively exploited by hackers to field massive DDoS attacks, due to an overlooked exploit,” Incapsula said in an e-mail statement.
The blame doesn’t lie solely (or even mostly) with Ubiquiti. Internet Service Providers (ISPs), vendors and end users all share blame in a pattern of loose security around SOHO devices that Incapsula called “inexplicably negligent.”
Incapsula said the DDoS campaign in question affected the domains of around 60 Incapsula-customers. It began in December and has continued, intermittently, ever since. The compromised devices are controlled using around 60 command and control (or C2) servers, mostly located in the US and China. In all, Incapsula documented attack traffic from 109 countries around the world.
Compromised routers had the MrBlack malware installed on them, a common malicious program.
Incapsula noted that home routers are often easy prey: ISPs tend to group them on dedicated IP address blocks, making it easy to scan a relatively small set of Internet addresses to find vulnerable devices.
Once built, the SOHO device botnet is well suited to do distributed scans and attacks, which can make it difficult to use blacklisting to block the offending activity.
Incapsula also noted similarities between the patterns of botnet activity and the activities of the hacktivist group the Lizard Squad. That group used Lizard Stressor, a global botnet that is also reportedly built on an infrastructure of under-secured routers. Despite several outward similarities, however, Incapsula concludes that the two botnets are not the same.
courtesy by : securityledger

